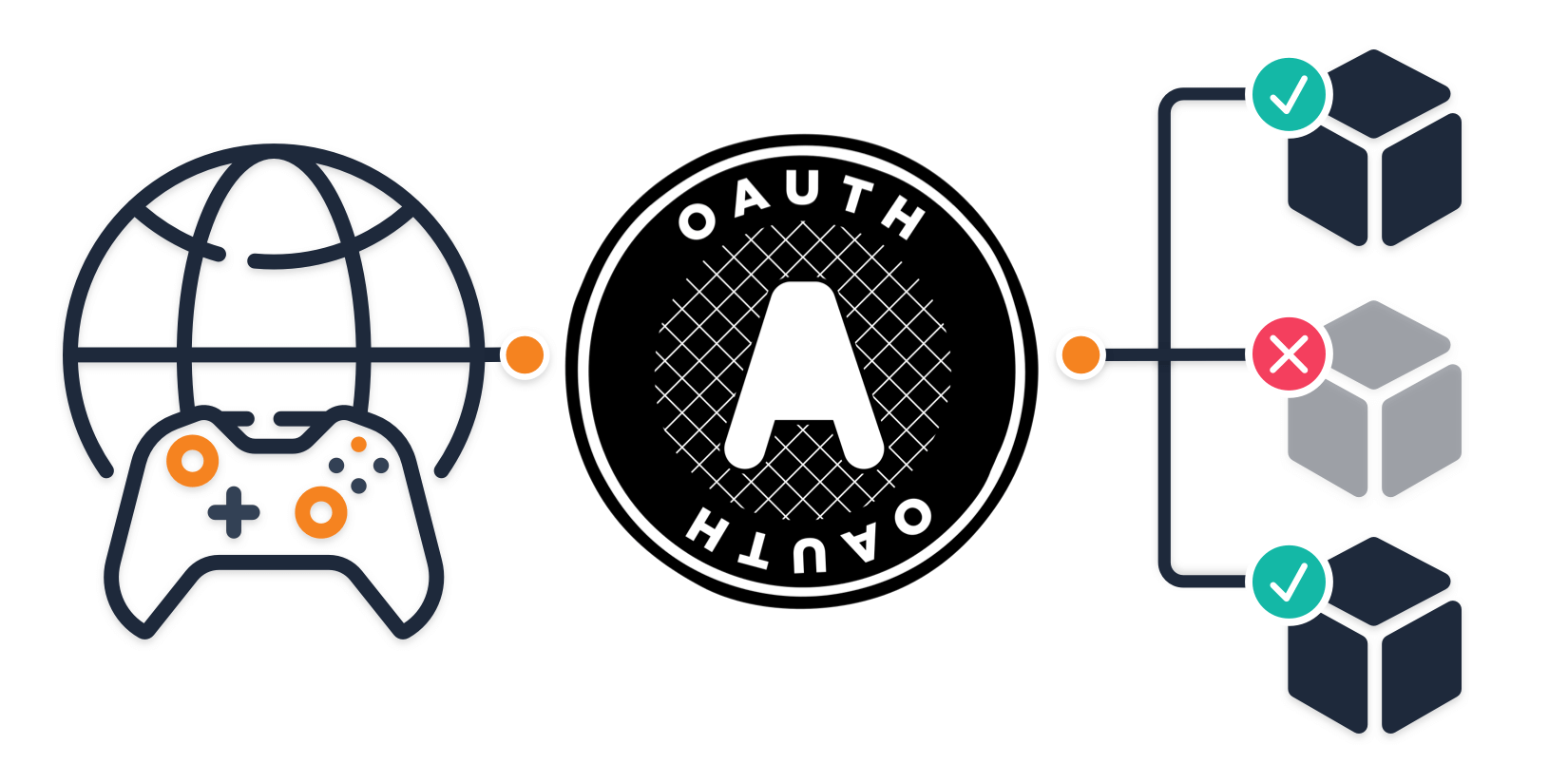
Is the OAuth Device grant right for your game authentication needs?
The OAuth device authorization grant is an extension of OAuth 2.0. Because OAuth is an authorization protocol, it enables users to gain access to an...
September 1, 2022
Categories

The OAuth device authorization grant is an extension of OAuth 2.0. Because OAuth is an authorization protocol, it enables users to gain access to an...
September 1, 2022

Congrats! Your new massively multiplayer online (MMO) game is ready and you’re all set to launch. However, you’re not sure whether your servers can handle the...
August 24, 2022
While esports competitions are high skill cap events, both hobby gamers and elite professionals alike expect optimal network conditions when they play games. A...
July 19, 2022

SCIM is a specification to add and remove users and groups using a standard protocol.
June 27, 2022

OAuth, a standard for securely delegating authorization information, and OIDC, a profile written on top of it to securely transmit user profile data, both rely...
June 14, 2022

As the industry continues to grow, gaming is becoming a way for users to make money in addition to being a form of entertainment. Gamers need to be able to...
June 1, 2022

Both Customer Identity and Access Management (CIAM) and IAM (Identity and Access Management) are about people who are users of your system: who can access...
May 10, 2022
Get updates on techniques, technical guides, and the latest product innovations coming from FusionAuth.
Just dev stuff. No junk.