OpenID Connect doesn't fallback to non-PKCE if provider doesn't support it
-
I've got an OpenID Connect identity provider which doesn't support PKCE.
I've read in the documentation that FusionAuth supports this and automatically falls back:
Proof Key for Code Exchange, more commonly referred to as PKCE (pronounced pixy) is an extension to the Authorization Code grant. This extension is intended to help secure the code exchange workflow utilized by this OpenID Connect configuration.
This extension is used by default on all OpenID Connect IdP configurations, and it cannot be disabled. The use of this extension is backwards compatible with identity providers that either do not require or support PKCE.
FusionAuth will pass along the required PKCE request parameters to the OpenID Connect identity provider and if the provider supports PKCE, the extension will be utilized, and if it is not supported it will be ignored.From: https://fusionauth.io/docs/lifecycle/authenticate-users/identity-providers/overview-oidc
However when I use this my login always fails with "The code_verifier could not be determined", which suggests to me that it attempts to use PKCE.
How can I (just for testing) force disabling PKCE?
How does FusionAuth detect if an identity provider supports PKCE?
How can I further debug this?
-
Has anyone had a similar issue? Would really appreciate a bit of insights here. Ideally I'd like to force FusionAuth to stop using PKCE with the identity provider I configured.
-
@yves said in OpenID Connect doesn't fallback to non-PKCE if provider doesn't support it:
How can I (just for testing) force disabling PKCE?
Have you tried to update the PKCE setting in your applicaiton?
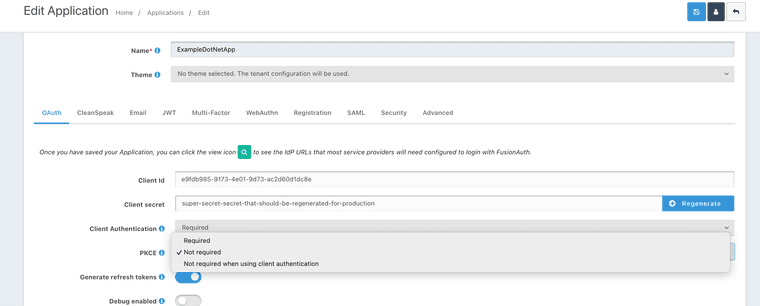
-
Thank you for the pointer @mark-robustelli .
However, also with this setting, I still get the following error message:
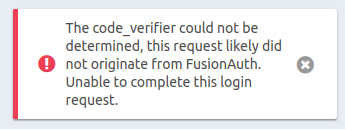
What am I doing wrong? Is this not referring to PKCE? Is this referring to something else? Where could I get further debug info? (Unfortunately the event log is empty.)
-
@yves Would it be possible for you to share a simplified code sample?
-
@mark-robustelli Sure!
I do the following (I use HTTPie)
- First I hit the
authorizeendpoint:http "https://myurl/oauth2/authorize?client_id=<myappid>&idp_hint=<myidpid>&nonce=<random generated nonce>&redirect_uri=/admin/login&response_type=code" - That gives me a
Locationwhich I follow:http "https://myurl/oauth2/redirect?client_id=<myappid>&identityProviderId=<myidpid>&state=<state>&nonce=<random generated nonce>" - Now again in the
LocationI get redirected to my IdP, I open that link in the browser and go through the flow of my IdP, once successfully authenticated it redirects me back tohttps://myurl/admin/login(the initial redirect URI) and I get the error I pasted earlier
Does this look correct to you?
- First I hit the
-
@yves So I found this that may be of interest to you.
For the Authorization Code Grant, if the clientAuthenticationPolicy value is Required, the client secret is required. If the value is NotRequired, the client secret is not required. If the value is NotRequiredWhenUsingPKCE and PKCE is used, the client secret is not required. If PKCE is not used, the client secret is required.
What is your setting there?