Deplyment behind Apache
-
Description
I have deployed the application (v. 1.55.1) behind an Apache proxy. I managed to do the intial configuration then I started to fine tune it. Then after I cliecked somewhere I got this error: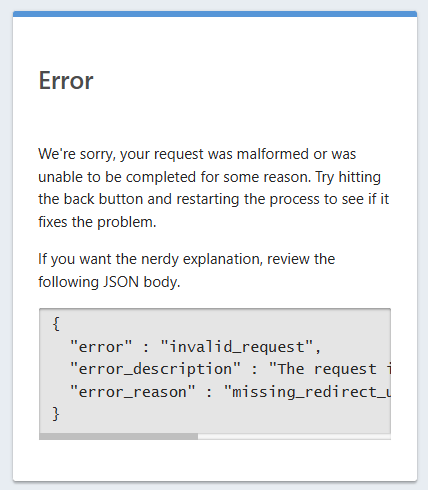
Now I'm not able to access anymore, because that error repeats any time I type the address https://auth.easycbam.eu/admin, despite I see that redirect_uri is present. This is the URL I am redirected to by FA:
Here's my Apache configuration, taken from https://github.com/FusionAuth/fusionauth-contrib/blob/main/Reverse Proxy Configurations/apache/apache.ssl.conf then edited with values from my installation:
# Change the following: # bbdb8f55-65e7-4de7-a5ff-f08df4ea8005 -> to the client_id of your application # 9f144ac0-3006-e653-2ce1-ba98bb40f3eb -> to the tenant ID of your tenant # http://localhost:9011/ -> to the location of your FusionAuth service # auth.easycbam.eu -> to the domain of your FusionAuth server # /usr/local/fusionauth/fusionauth-app/web -> to the path to your FA static content # Optional: If you want to serve static files directly without FusionAuth #<Directory "/usr/local/fusionauth/fusionauth-app/web/"> # Require all granted # allow from all # AllowOverride none #</Directory> # Redirect all traffic to SSL, except LE challenges <VirtualHost *:80> ServerName auth.easycbam.eu Redirect permanent / https://auth.easycbam.eu/ RewriteEngine on RewriteCond %{SERVER_NAME} =auth.easycbam.eu RewriteRule ^ https://%{SERVER_NAME}%{REQUEST_URI} [END,NE,R=permanent] # Optional: If you want to use LetsEncrypt keep this, otherwise remove it #Alias /.well-known /var/www/letsencrypt/.well-known </VirtualHost> <VirtualHost *:443> ServerAdmin daniele.bonfatti@ket-consulting.com ServerName auth.easycbam.eu # Optional: This avoids proxying local files which Apache can serve without # bother FusionAuth. There may be reasons to let FA deal with these files, in which # case these should be removed. #Alias /js /usr/local/fusionauth/fusionauth-app/web/js #Alias /css /usr/local/fusionauth/fusionauth-app/web/css #Alias /images /usr/local/fusionauth/fusionauth-app/web/images RewriteEngine on # Optional (here for security reasons) #RewriteCond %{REQUEST_METHOD} ^(TRACE|TRACK) #RewriteRule .* - [F] # Users logging into the auth URL will end up at /login?code=...&userState=Authenticated # and will receive a 500 error from FusionAuth. This redirect sends them off to the application # to do whatever it was they wanted to do at the auth URL. RewriteCond %{REQUEST_METHOD} =GET RewriteCond %{QUERY_STRING} (^|&)userState=Authenticated($|&) RewriteRule /login https://www.easycbam.eu/app? [R,L] # Set to the URL of your application # This rewrite corrects the client_id in proxied requests. It only does so if there was one # to start with, and it's not clever enough to realise it's already corrected it RewriteCond %{REQUEST_METHOD} =GET RewriteCond %{QUERY_STRING} ^(.*)client_id=([^&]*)($|&)(.*)$ RewriteRule ^(.*)$ $1?%1client_id=bbdb8f55-65e7-4de7-a5ff-f08df4ea8005 [E=rewritten:1] # This corrects a tennantID if there's one set already. This prevents users for fiddling with it # (or rather, users can write what they want in a URL, this ensures we only send the correct one # to FusionAuth) RewriteCond %{REQUEST_METHOD} =GET RewriteCond %{QUERY_STRING} ^(.*)tenantId=([^&]*)($|&)(.*)$ RewriteRule ^(.*)$ $1?%1tenantId=9f144ac0-3006-e653-2ce1-ba98bb40f3eb [E=rewritten:1] # This adds a tenantID if there isn't one already. It only does this if there is something in # the query string though. This avoids adding one to static content and the like. RewriteCond %{REQUEST_METHOD} =GET RewriteCond %{QUERY_STRING} !^$ RewriteCond %{QUERY_STRING} !tenantId= RewriteRule ^(.*)$ $1?%{QUERY_STRING}&tenantId=9f144ac0-3006-e653-2ce1-ba98bb40f3eb [E=rewritten:1] # Finally, this "noop" tells Apache to treat the rewritten URL as a URI and to re-run it through # the checks for proxies etc, otherwise it'll be treated as a local file (which will fail) RewriteCond "%{ENV:rewritten}" "=1" RewriteRule ^(.*)$ $1 [PT] # Optional: if you're using LE then keep this, otherwise remove it #Alias /.well-known /var/www/letsencrypt/.well-known # These X- headers are required - without them CSRF won't work RequestHeader set X-Real-IP "%{REMOTE_ADDR}s" RequestHeader set X-Forwarded-Proto "https" RequestHeader set X-Forwarded-Port "443" RequestHeader set X-Forwarded-For "%{REMOTE_ADDR}s" # This header is useful for API calls that don't have query strings (and so will miss the rules above) RequestHeader set X-FusionAuth-TenantId 9f144ac0-3006-e653-2ce1-ba98bb40f3eb ProxyPass / http://localhost:9011/ ProxyPassReverse / http://localhost:9011/ # We have to send a "Host: xxx" header with the orginal server hostname in it ProxyPreserveHost On <Location /> # This stops Apache sending X-Forwarded-Host and X-Forwarded-Server, which seem to trip up FusionAuth # It also stops X-Forwarded-For, which we need, but set that ourselves above. This also has to go # inside a <Location> otherwise it doesn't work. ProxyAddHeaders off </Location> SSLCertificateFile /etc/letsencrypt/live/auth.easycbam.eu/fullchain.pem SSLCertificateKeyFile /etc/letsencrypt/live/auth.easycbam.eu/privkey.pem Include /etc/letsencrypt/options-ssl-apache.conf </VirtualHost>Any idea on how to solve it?
-
Eventually I managed to make it work, by commenting everything out from
RewriteEngine onto
RewriteRule ^(.*)$ $1 [PT]both included.
In practice I commented out all the stuff on rewriting.So the configuration taken from
https://github.com/FusionAuth/fusionauth-contrib/blob/main/Reverse Proxy Configurations/apache/apache.ssl.conf
doesn't work in my use-case (which, I think, is pretty standard). -
@bonfattidaniele Is auth.easycbam.eu your domain? Is bbdb8f55-65e7-4de7-a5ff-f08df4ea8005 your client_id? Is 9f144ac0-3006-e653-2ce1-ba98bb40f3eb your tenantId? It appears that those values may not have been updated if not. I am not an Apache expert so I am not sure what implications removing those statements is going to have. Can you try updating those ids, domains and other variables in the config to see if that works?