Proxy Configuration Warning help
-
@ronn316 said in Proxy Configuration Warning help:
proxy
I may be missing something, but the actual request origin includes the port number :9011. If you remove that from the request, does it work?
-
@mark-robustelli I am simply navigating to https://auth.mysite.com/admin/ and logging into my account. How would I go about removing the port from the request?
-
@ronn316 It looks like the reported and actual request origins are not the same. I am not very familiar with proxies, but it appears to me that you need to change the port FusionAuth may still be listening on. I see you created the FUSIONAUTH_APP_HTTPS_PORT environmental variable, but what is reading that? Are you sure it is changing the FusionAuth port?
What is the value in the config file?
According to [https://fusionauth.io/docs/reference/configuration#options](the docs) port is set
linux or mac
/usr/local/fusionauth/config/fusionauth.propertiesor
windows\fusionauth\config\fusionauth.propertiesand the value would be under
fusionauth-app.https-port -
@mark-robustelli Thanks for the insight Mark.
Indeed I also believe I need to change the port FusionAuth is listening on.
Since I'm hosting the FusionAuth container on Azure App Service, I haven't found a way to access the file system and change the port in the config file so I chose the environmental variable route. According to the Azure documentation, this is how you add environmental variables to your container, as in my image above.
I had already had a look at that link previously when trying to understand how to change the port, and that's how I learned how to structure the environmental variable name.
"2. Check if an environment variable is defined with the configuration option name translated by upper-casing it and replacing periods and dashes with underscores"
Following that instruction, I created an environmental variable for the option "fusionauth-app.https-port" by uppercasing all letters and replacing the dashes and dots by underscores, hence the FUSIONAUTH_APP_HTTPS_PORT environmental variable you see in my image.
I think the container is reading the variable just fine, because I recall adding some other env variables as well and noticing some things breaking as a result. I don't recall exactly what I added though. So it seems that the changes are taking effect, but maybe this one setting is not enough.
I will have a look over the next days if I can somehow access the filesystem and change the setting in the config file but I don't think it will help because as I said it looks as though the environmental variable is indeed taking effect. The key is to figure out exactly which settings need to be adjusted.
-
@ronn316 Thanks for the info. I hope to have some time next week and I will see if I can replicate this in Azure and get it rolling. I will keep you updated if I come across anything interesting.
-
@mark-robustelli Thank Mark, let me know if you may need anything from my side.
-
I'm by no means an expert on networking and proxies, however I've been doing some reading on this topic the last couple of days, and it seems I have two choices.
-
Configure my own proxy which I've tried with no success. I attempted to setup an Nginx server within an App Service but I need to specify paths to ssl certificate and private key in the .conf file which I don't know how to access within Azure app service. The certificate in my app service are managed by Microsoft. I've seen in Microsoft's documentation that you can set an env variable WEBSITE_LOAD_CERTIFICATES which will make the certificate files available at a certain path in your container which I will explore.
-
Use the newly added configuration options for TLS such as fusionauth-app.https.port that I already set. This seems like the way to go so I don't need to setup a different container for a proxy. It looks like I need to also configure fusionauth-app.https.enabled, fusionauth-app.https.certificate-file, and fusionauth-app.https.private-key-file. However, as mentioned in point 1, the certificate in my app is managed by Microsoft, and seems the formats of the certificate file that Fusionauth expects (.pem) vs the format of the file that is available at /var/ssl/certs by enabling WEBSITE_LOAD_CERTIFICATES env variable (.p12) do not match.
-
-
@ronn316 still working on setting this up, but came across this and wanted to see if it was any help. https://fusionauth.io/community/forum/topic/2367/fusionauth-on-azure-app-service-for-containers?_=1703616145335
-
@mark-robustelli I looked into Application Gateway but discovered its pricing would more than double my monthly cost for my app, so I discarded it.
Atm I'm experimenting with two different approaches:
-
setting up an Nginx proxy with SSL on Azure app service, so I can change the necessary headers. I've generated ssl certificates for my proxy through Lets encrypt, and reference them in my nginx config but I'm not doing something right because it just times out.
-
configuring the https settings in the fusionauth.properties file. By building my own docker image, I'm able to edit the configuration file and inject it into my image. From my understanding, we need to populate not only the setting to enable https, but also the port, and the paths to the ssl certificate files. I copied the Lets encrypt certificates into my image and set the paths in the config file but Fusionauth doesn't like something still. It might be the format of the certificate files. I'm still experimenting with this.
I hope you can make some headway with Azure.
-
-
@ronn316 Do you have an configuration file that would help me set my environment up the same way you have yours?
-
@mark-robustelli So I have spent more time playing with Azure and trying to get this up and running with no luck. I do see that configuring the Ingress for that app container only allow inbound from 443. I thought there was a setting we could use to just forward the port, but you can only set it for the other container apps in the environment.
If you can send me some sort of config file or how you have your environment currently set up, I will try to poke around a bit more if I get some time. I feel that has more to do with Azure configuration that FusionAuth config. Have you tried reaching out on some other Azure friendly channels?
-
@mark-robustelli @mark-robustelli It sounds like you were experimenting with Azure Container apps judging by the fact you mentioned ingress and container environments? I'm actually using Azure App Service, and I chose the container option for that. App Service and Container Apps are quite different in their settings.
I'll show you what I did in order to setup the TLS settings of Fusionauth, not the proxy approach I also tried. That one is a bit more involved.
I created a dockerfile and edited the fusionauth.properties. In my dockerfile I'm pulling the fusionauth image and copying into the container my SSL certificates generated using Let's Encrypt. Also you can see I'm copying in my updated fusionauth.properties file.

Here is my fusionauth.properties file:
I'm building the image and storing it on Azure to be accessible on Azure App Service. I'm not sure if I can export any settings from my Azure setup but I'll post screenshots.
Here are the deployment settings of my App service. You can see I'm pulling the fusionauth image I created.

These are the platform settings.

After doing all this, I am now getting an error related to the SSL certificates.
"Exception in thread "main" java.lang.RuntimeException: java.lang.IllegalArgumentException: Invalid PEM format"
I think there might be an issue with the format I'm using (.pem), but this is the format Let's encrypt is outputting, unless something else is wrong. These are the files I'm getting from Lets encrypt.

-
So I made a bit more progress but it's disappointing news.
I managed to get the certificates to work correctly. I needed to convert the .pem private certificate to PKCS8. After doing that I don't get any error in the log when Fusionauth initializes, and I'm able to log into the dashboard unlike before, but disappointingly I'm still seeing the same Proxy Configuration Warning at the top of the page. I thought that using the inbuilt TLS listener would bypass the need for a proxy, or is that not correct? According to this request which has since been added, I'm given the impression that configuring HTTPS will bypass the need for a reverse proxy. Is there a way for me to confirm that the app is listening to https requests?

-
@ronn316 I am still struggling getting this far in the Azure setup. However it is good that you are making progress. Is there a way to view the logs from the azure portal to see if requests are incoming?
-
@mark-robustelli Yeah seems like I'm getting closer but not sure what else to try regarding enabling HTTPS. Everything seems ok from my setup. I can't see any logs in Azure about incoming requests. I can only see startup logs.
-
@ronn316 Ok, I finally have been able to replicate your issue. I see you set the environment variable FUSIONAUTH_APP_HTTPS_PORT above to 443:
I did this as well.
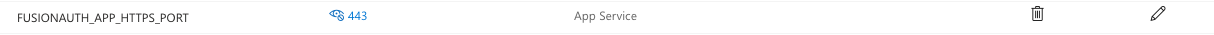
However, when I look at the logs, it appears to still be listening on 9011.
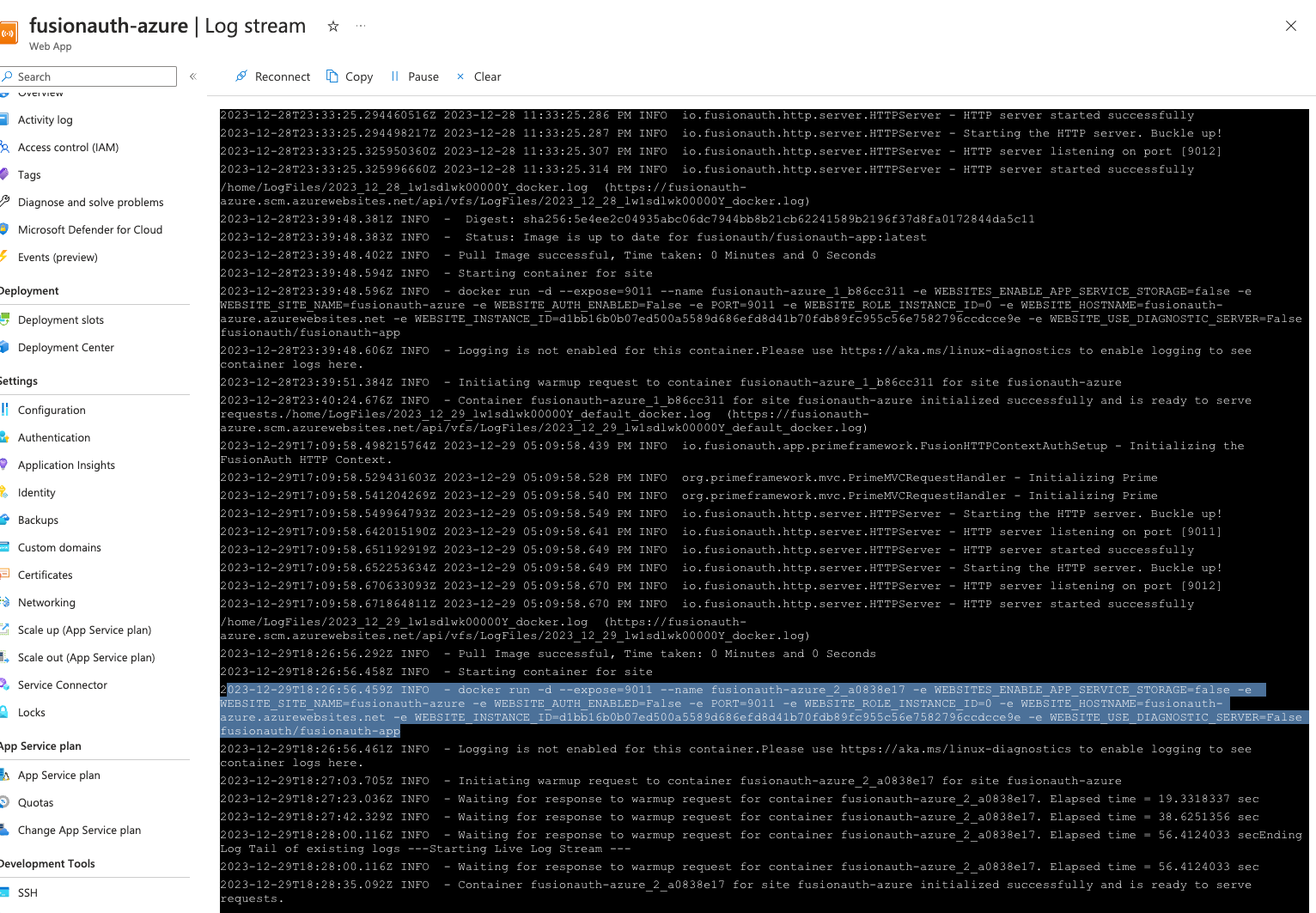
Do you see the same thing in your log?
You may have to create a docker image with the correct configuration and then upload that as the container to use.
I'll still play with it when I get some time but I think we need FusionAuth to be listening on 443 for this to work. Just not sure how to make that happen in Auzre App Service.
-
@mark-robustelli Good catch, yes I see that too in my logs. I did a search and you can update the port that the container is listening on by adding an environmental variable WEBSITES_PORT.

After doing that and restarting the container, I can see in the log that port it is using 443 now.

But still I'm getting the same proxy warning in the dashboard
 But I think we're really close to figuring this out. It would be good to get the thoughts of Fusionauth engineer on this matter.
But I think we're really close to figuring this out. It would be good to get the thoughts of Fusionauth engineer on this matter.Btw I'm not sure if in your configuration you also setup the certificate environmental variables. I think in order to enable https, you need to set the port as well as the certificate files or the contents of the files.

-
@mark-robustelli So you would need to either set the four environmental variables in Azure, or set the four properties in the .properties file. I chose the latter in the end.
-
@mark-robustelli Seems I didn't restart my container properly the first time. I did that again and I'm seeing some new errors in the docker logs regarding SSL.

So I think now the container is indeed listening on 443 since adding the new environmental variable WEBSITES_PORT, but something else is going wrong now. I need to look into what this error means:
javax.net.ssl.SSLException: Unrecognized SSL message, plaintext connection? -
@ronn316 I think I may have some bad news going down this route.
It seems like it may be possible but is not recommended to so this.
I'm going to take another route now and see if there is anything we can do with App Services and redirecting the port.
BTW, have you tried the Kubernettes route (https://fusionauth.io/docs/get-started/download-and-install/kubernetes/aks) to run FusionAuth in Azure or just use a regular container and Postgres db? I have not myself, but seems like that may be a route to go too.