Authorization Code with PKCE and without Client Secret in Postman
-
I'm trying to get my browser extension to authenticate against FA using OAuth2. Authorization Code with PKCE seems to be the answer, but I keep getting stuck at the
tokenendpoint.I'm getting a 401 error:
{"error":"invalid_client","error_description":"Invalid client authentication credentials.","error_reason":"invalid_client_authentication"}Authentication works great from Postman when adding the Client Secret to the Authentication options, but that defeats the purpose of PKCE.
Do you have a Postman example and FA Application setup to test?
-
What does your application config look like?
If you don't want client authentication to be enforced, you need to configure the application to do this.
https://fusionauth.io/docs/v1/tech/core-concepts/applications/#oauth
Client Authentication
This selector allows you to set a rule for accessing the Token endpoint.
Required - The client_secret parameter must be used. This is the default setting. In most cases you will not want to change this setting.
Not required - Use of the client_secret parameter is optional.
Not required when using PKCE - Requires the use of the client_secret parameter unless a valid PKCE code_verifier parameter is used. This is useful for scenarios where you have a requirement to make a request to the Token endpoint where you cannot safely secure a client secret such as native mobile applications and single page applications (SPAs) running in a browser. In these scenarios it is recommended you use PKCE.
See the Token endpoint for more information. -
@dan, I have tried every possible combination of Client Authentication and PKCE settings. Nothing seems to work. Currently I have this config:
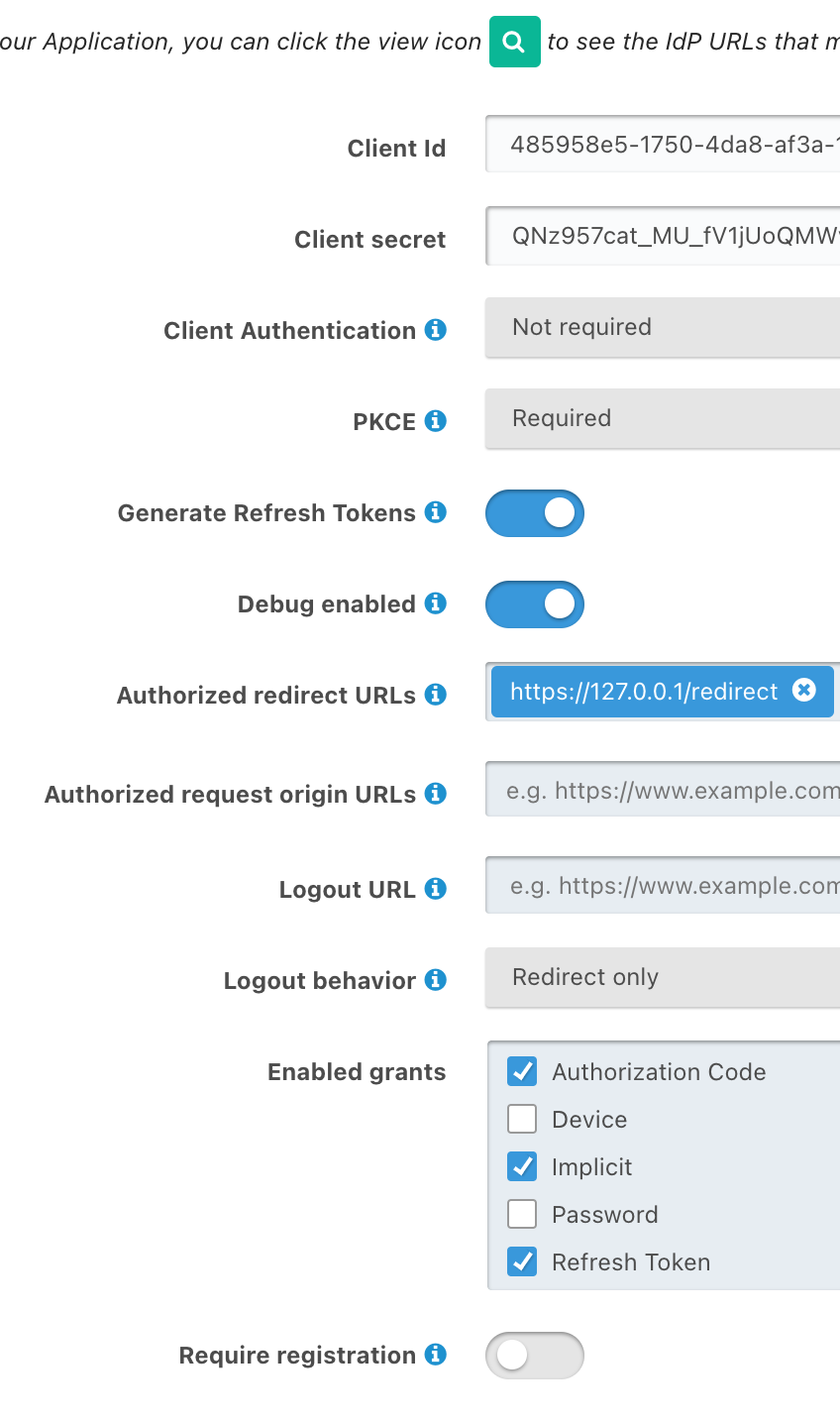
-
Is there anything interesting in the Debug Event log?
I'll also note if you do not want to require client authentication, ensure you are not sending a
client_secret. Regardless of your configuration, if provided it will be validated. -
@felix said in Authorization Code with PKCE and without Client Secret in Postman:
"Invalid client authentication credentials."
From the error you posted, it appears you are using the client credentials grant. This grant is not part of the OAuth2 application configuration and does not support PKCE. The client credentials grant will require a
client_idandclient_secretfrom the Entity.https://fusionauth.io/docs/v1/tech/oauth/endpoints/#client-credentials-grant-request
-
Ok, I found the problem.
I was sending an
Authorizationheader, because that was the default option in Postman. Now I tried it with the other option which is "Send client credentials in body" and it works.The documentation about the token endpoint had me a bit confused, that's why I kept sending an (invalid)
Authorizationheader. Now that I post an emptyclient_secretparameter in the body and NOAuthorizationheader to thetokenendpoint, things are working fine.Thanks for pointing me in the right direction, @robotdan and @dan.