Gateway with OAuth2 Resource Server for custom tenant
-
Hi, I have created a tenant in fusionauth with the issuer "anyissuer", then I configured a spring cloud gateway with spring boot 3.2.1 with:
spring.security.oauth2.resourceserver.jwt.issuer-uri=http://localhost:9011/.well-known/openid-configuration/018d642c-e707-7349-95c7-ead15f625746
spring.security.oauth2.resourceserver.jwt.audiences[0]=018d642c-a7e8-75b1-96af-1ea04c3b0faaso doing this, when I tried to access some secure url, I am having the error: The Issuer "anyissuer" provided in the configuration did not match the requested issuer "http://localhost:9011/.well-known/openid-configuration/018d6028-e976-7aef-8d35-d65386e6b448"
however in http://localhost:9011/.well-known/openid-configuration/018d6028-e976-7aef-8d35-d65386e6b448 the issuer in the response is "anyissuer".
I have found in the org.springframework.boot.autoconfigure.security.oauth2.resource.reactive.ReactiveOAuth2ResourceServerJwkConfiguration class that in this method
@Bean @ConditionalOnProperty( name = {"spring.security.oauth2.resourceserver.jwt.jwk-set-uri"} ) ReactiveJwtDecoder jwtDecoder(ObjectProvider<JwkSetUriReactiveJwtDecoderBuilderCustomizer> customizers) { NimbusReactiveJwtDecoder.JwkSetUriReactiveJwtDecoderBuilder builder = NimbusReactiveJwtDecoder.withJwkSetUri(this.properties.getJwkSetUri()).jwsAlgorithms(this::jwsAlgorithms); customizers.orderedStream().forEach((customizer) -> { customizer.customize(builder); }); NimbusReactiveJwtDecoder nimbusReactiveJwtDecoder = builder.build(); String issuerUri = this.properties.getIssuerUri(); OAuth2TokenValidator<Jwt> defaultValidator = issuerUri != null ? JwtValidators.createDefaultWithIssuer(issuerUri) : JwtValidators.createDefault(); nimbusReactiveJwtDecoder.setJwtValidator(this.getValidators(defaultValidator)); return nimbusReactiveJwtDecoder; }it is creating the issuer validator with the value of spring.security.oauth2.resourceserver.jwt.issuer-uri property instead of the value of issuer in the response of http://localhost:9011/.well-known/openid-configuration/018d642c-e707-7349-95c7-ead15f625746
So to sum up, is there a way to configure oauth2 resource server with spring boot 3.2.1 to get the openid-configuration from the tenant (resolved specifying http://localhost:9011/.well-known/openid-configuration/018d642c-e707-7349-95c7-ead15f625746 in the spring.security.oauth2.resourceserver.jwt.issuer-uri property) and having a jwtDecorder working properly with de issuer?
The only way I have made this "working" is changin my tenant issuer to be http://localhost:9011/.well-known/openid-configuration/018d642c-e707-7349-95c7-ead15f625746
-
Hiya, welcome to the FusionAuth community!
Hmm, per this doc, you can only use the
issuer-uriin specific situations.To use the issuer-uri property, it must also be true that one of idp.example.com/issuer/.well-known/openid-configuration, idp.example.com/.well-known/openid-configuration/issuer, or idp.example.com/.well-known/oauth-authorization-server/issuer is a supported endpoint for the authorization server. This endpoint is referred to as a Provider Configuration endpoint or a Authorization Server Metadata endpoint.
FusionAuth doesn't support those formats for an arbitrary string. However you could use the tenant id as the
issuer, sincehttp://localhost:9011/bafb4319-b7ca-ed27-fa2f-bbdba9d8ec06/.well-known/openid-configurationis a valid endpoint.bafb4319-b7ca-ed27-fa2f-bbdba9d8ec06is the tenant Id.Hope that helps.
-
Hi @dan , unlucky with that, it only works with the same value in
spring.security.oauth2.resourceserver.jwt.issuer-uri=http://localhost:9011/018d6028-e976-7aef-8d35-d65386e6b448/.well-known/openid-configurationand issuer field in the tenant configuration:
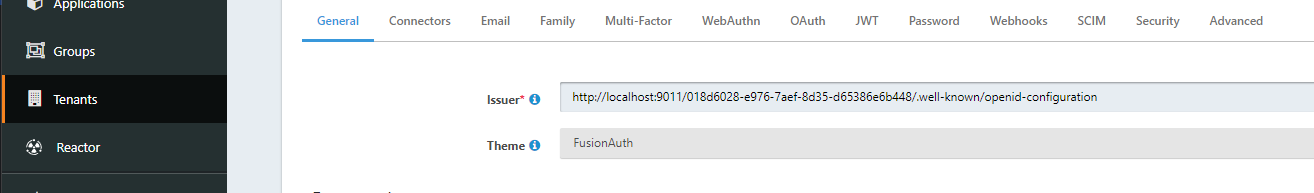
If I change the issuer in the tenant configuration to acme.com in example, http://localhost:9011/018d6028-e976-7aef-8d35-d65386e6b448/.well-known/openid-configuration returns "issuer" : "acme.com" in the response but oauth2 or spring security keeps comparing the token iss with spring.security.oauth2.resourceserver.jwt.issuer-uri property:
"java.lang.IllegalStateException: The Issuer "acme.com" provided in the configuration did not match the requested issuer "http://localhost:9011/018d6028-e976-7aef-8d35-d65386e6b448/.well-known/openid-configuration"what make sense related with the code in org.springframework.boot.autoconfigure.security.oauth2.resource.reactive.ReactiveOAuth2ResourceServerJwkConfiguration, but from my point of view, the issuer validation should be againt the response not the property
-
Hi @dan , doing like this https://stackoverflow.com/questions/77919421/spring-cloud-gateway-with-fusionauth-custom-tenant works fine
-
@asenjowork Awesome, I'm glad you figured it out!