Unexpected validity of access_token obtained via exchanging refresh_token
-
When exchanging a
refresh_tokenfor anaccess_token, I expect the resultingaccess_tokento have a validity as defined by the application.
However, this doesn't seem to be the case..

Currently, I'm not sure where the 12-hour duration for the JWT is coming from. Is this a default value? If so, how would I override it?
-
What version of fusionauth are you running?
Does the JWT have the correct duration when first issued? Is it only when a refresh token is used that the duration is incorrect?
The tenant also has some JWT duration settings, maybe the application is being incorrectly bypassed.
Looking forward to hearing your response, maybe we can track this down with repro steps and file a bug.
-
I'm running FusionAuth v1.18.8
The
access_tokenthat is first issued has the right expiry. Anyaccess_tokenreceived via exchangingrefresh_tokenhas a 12 hour validity.
My tenant does have a 12 hour validity on theaccess_token. However, any tenant setting should be overridden by the application-specific setting, is it not? -
Can you try changing the tenant session to 13 or 11 hours and see if the lifetime of the second JWT changes?
Yes, the application specific setting should control, for sure.
I don't see any refresh token changes between 1.18.8 and 1.22.0, but is it possible for you to upgrade to that version and see if this behavior still occurs?
-
Changing the JWT lifetime in the tenant reflects in the lifetime of the
access_tokenobtained by exchangingrefresh_token.
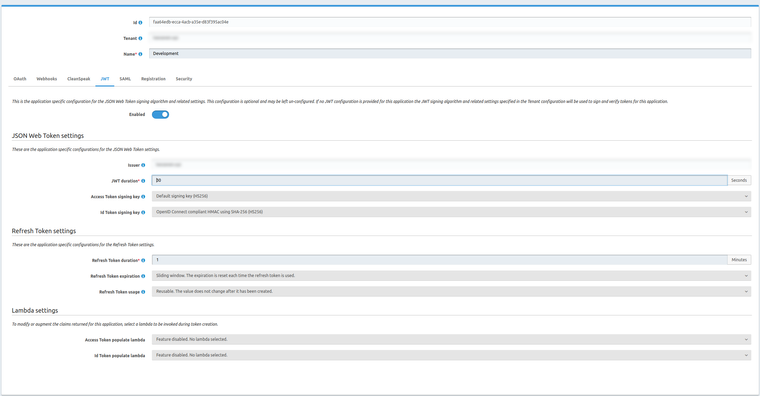
For example, with the following config, here's what I get in my logs:Application Settings
Tenant Settings
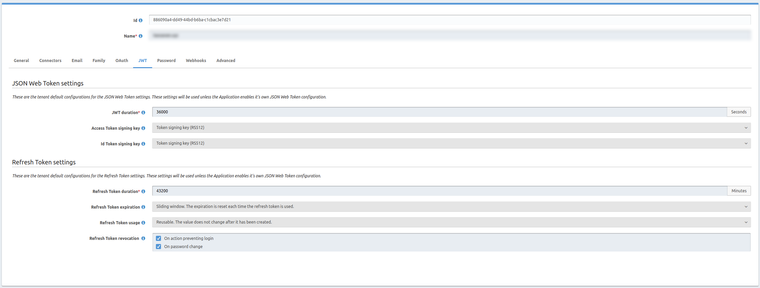
Token expires in 28475 {aud: "faa64edb-ecca-4acb-a35e-d83f395ac04e", iat: 1607337214, exp: 1607337244} Refreshing tokens to avoid expiry {aud: "faa64edb-ecca-4acb-a35e-d83f395ac04e", iat: 1607337214, exp: 1607337244} Token expires in 35999195 {aud: "faa64edb-ecca-4acb-a35e-d83f395ac04e", iat: 1607337215, exp: 1607373215} -
Thanks!
One last question. Are you passing the
client_idto the refresh token endpoint on all requests? (I looked through the thread, but didn't see evidence either way.) If not, does doing so affect this behavior?https://fusionauth.io/docs/v1/tech/oauth/endpoints/#refresh-token-grant-request
-
Yes, I'm explicitly passing the
client_idas a request parameter as part of every request---initial login request as well as subsequent refresh token grant requests.Is this happening because I use the Login API as opposed to OAuth API?
-
I think this is a bug. For some reason the tenant settings are controlling on the refresh token exchange when the application config should take precedence.
Can you please file an issue here: https://github.com/fusionauth/fusionauth-issues/issues and reference this forum post?