@dan I can confirm it's working as expected. Thanks for your useful advice.
Posts made by laurent.michel
-
RE: Why can't I update the default tenants smtp parameters through the API?posted in Q&A
-
RE: Why can't I update the default tenants smtp parameters through the API?posted in Q&A
@dan hmmm I did not see that method. I'll give a try. I'm pretty sure it will work. Thanks for the hint!
-
RE: Why can't I update the default tenants smtp parameters through the API?posted in Q&A
long story short: this works:
request = { 'tenant': { 'emailConfiguration': { 'host': hostname, 'port': port, 'username': username, 'password': password, 'security': 'SSL' if enable_ssl == 'true' else 'NONE', } } } headers = {'content-type': 'application/json', 'authorization': api_key} response = requests.patch(f'{api_url}/api/tenant/{tenant_id}', data=json.dumps(request), headers=headers)i.e. I receive status
200, but this doesn't:request = { 'tenant': { 'emailConfiguration': { 'host': hostname, 'port': port, 'username': username, 'password': password, 'security': 'SSL' if enable_ssl == 'true' else 'NONE', } } } response = client.update_tenant(tenant_id, request)i.e. I receive status
400. -
RE: Why can't I update the default tenants smtp parameters through the API?posted in Q&A
Without the trailing slash in fusionauth api url, I get a 400 status code for call
request = { 'tenant': { 'emailConfiguration': { 'host': hostname, 'port': port, 'username': username, 'password': password, 'security': 'SSL' if enable_ssl == 'true' else 'NONE', } } } response = client.update_tenant(tenant_id, request)The printed value of the
requestvariable is{'tenant': {'emailConfiguration': {'host': 'my-smtp-host', 'port': 8081, 'username': 'laurent', 'password': '1234', 'security': 'SSL'}}} -
RE: Why can't I update the default tenants smtp parameters through the API?posted in Q&A
I was able to gather that
response = client.retrieve_tenants() tenants = response.success_response['tenants']returns
Nonebecause I created the fusionauth client like this:client = FusionAuthClient(args.api_key, args.api_url)with
api_urlending with trailing slash. Interestingly,response.was_successful()is true. I still have no explanation for the other call.
-
RE: Why can't I update the default tenants smtp parameters through the API?posted in Q&A
If I do
curl http://docker122445-env-0749025.hidora.com/api/tenant -H "Accept: application/json" -H 'Authorization: CrH00Hgsp1yj1NKyGHGwxS8xKpoJh9gwNcOKful4'then I get my default tenant.
-
RE: Why can't I update the default tenants smtp parameters through the API?posted in Q&A
If I don't use the python client, but rather do this:
curl -X PATCH http://my-fusionauth-hostname.com/api/tenant/135ccc5c-17b9-414b-9538-65d77e53a0c0 -H 'Content-Type: application/json' -H 'Accept: application/json' -H 'Authorization: CrH00Hgsp1yj1NKyGHGwxS8xKpoJh9gwNcOKful4' -d '{ "tenant": { "emailConfiguration": { "host": "smtp-host", "port": 8080, "username": "the-username", "password": "password", "security": "SSL" } } }'Then it works.
-
Why can't I update the default tenants smtp parameters through the API?posted in Q&A
I am using the single, default tenant defined by fusionauth :
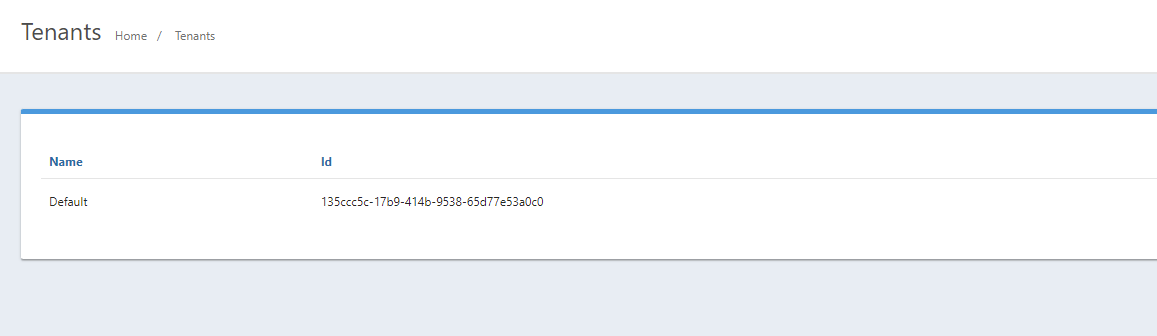
I installed fusionauth with the following kickstart:
{ "apiKeys": [ { "description": "Almighty API Key", "key": "#{almightyApiKey}" }, { "description": "Serverless API Key", "key": "#{serverlessApiKey}", "permissions": { "endpoints": { "/api/jwt/validate": [ "POST" ], "/api/login": [ "POST" ], "/api/user": [ "POST", "DELETE" ], "/api/user/registration": [ "POST" ] } } } ], "requests": [ { "body": { "registration": { "applicationId": "#{FUSIONAUTH_APPLICATION_ID}", "roles": [ "admin" ] }, "user": { "email": "#{adminEmail}", "password": "#{adminPassword}" } }, "method": "POST", "url": "/api/user/registration" }, { "body": { "emailTemplate": { "defaultHtmlTemplate": "To change your password use the following token:\n\n<p>changePasswordId=${changePasswordId}</p>", "defaultSubject": "Reset your password", "defaultTextTemplate": "To change your password use the following token: \n\nchangePasswordId=${changePasswordId}", "name": "Forgot Password" } }, "method": "POST", "url": "/api/email/template/#{forgotPasswordEmailTemplateId}" }, { "body": { "emailTemplate": { "defaultHtmlTemplate": "Your account has been created and you must setup a password. Use the following token to setup your password:\n\n<p>changePasswordId=${changePasswordId}</p>", "defaultSubject": "Setup your password", "defaultTextTemplate": "Your account has been created and you must setup a password. Use the following token to setup your password: \n\nchangePasswordId=${changePasswordId}", "name": "Setup Password" } }, "method": "POST", "url": "/api/email/template/#{setPasswordEmailTemplateId}" }, { "body": { "emailTemplate": { "defaultHtmlTemplate": "[#if user.verified]\nPro tip, your email has already been verified, but feel free to complete the verification process to verify your verification of your email address.\n[/#if]\n\nTo complete your email verification use the following token:\n\n<p>${verificationId}</p>", "defaultSubject": "Verify your email address", "defaultTextTemplate": "[#if user.verified]\nPro tip, your email has already been verified, but feel free to complete the verification process to verify your verification of your email address.\n[/#if]\n\nTo complete your email verification use the following token:\n\n${verificationId}", "name": "Email Verification" } }, "method": "POST", "url": "/api/email/template/#{verificationEmailTemplateId}" }, { "body": { "emailTemplate": { "defaultHtmlTemplate": "[#if registration.verified]\nPro tip, your registration has already been verified, but feel free to complete the verification process to verify your verification of your registration.\n[/#if]\n\nTo complete your registration verification use the following token: \n<p>${verificationId}</p>", "defaultSubject": "Verify your registration", "defaultTextTemplate": "[#if registration.verified]\nPro tip, your registration has already been verified, but feel free to complete the verification process to verify your verification of your registration.\n[/#if]\n\nTo complete your registration verification use the following token: \n\n${verificationId}", "name": "Registration Verification" } }, "method": "POST", "url": "/api/email/template/#{registrationVerificationEmailTemplateId}" }, { "body": { "tenant": { "emailConfiguration": { "defaultFromEmail": "#{fromEmail}", "defaultFromName": "#{fromName}", "forgotPasswordEmailTemplateId": "#{forgotPasswordEmailTemplateId}", "host": "#{mailServerHost}", "password": "#{mailServerPassword}", "port": "#{mailServerPort}", "security": "#{mailServerSecurity}", "setPasswordEmailTemplateId": "#{setPasswordEmailTemplateId}", "username": "#{mailServerUsername}", "verificationEmailTemplateId": "#{verificationEmailTemplateId}", "verificationStrategy": "FormField", "verifyEmail": true, "verifyEmailWhenChanged": true }, "issuer": "#{issuer}", "name": "Default", "userDeletePolicy": { "unverified": { "enabled": true, "numberOfDaysToRetain": 1 } } } }, "method": "PATCH", "url": "/api/tenant/#{defaultTenantId}" }, { "body": { "lambda": { "body": "function populate(jwt, user, registration) { jwt['#{hasuraClaimsNamespace}'] = { 'x-hasura-allowed-roles': jwt.roles, 'x-hasura-default-role': jwt.roles[0], 'x-hasura-user-id': user.id }; }", "debug": true, "enabled": true, "name": "hasura", "type": "JWTPopulate" } }, "method": "POST", "url": "/api/lambda/#{hasuraLambdaId}" } ], "variables": { "adminEmail": "admin@company.com", "adminPassword": "my admin password", "almightyApiKey": "24114b81-4207-4b02-bcd5-3bbbb91a66e7", "defaultTenantId": "9d72d134-464e-4542-a42f-6b0ac602f0d2", "forgotPasswordEmailTemplateId": "#{UUID()}", "fromEmail": "no-reply@company.com", "fromName": "Company", "hasuraClaimsNamespace": "https://hasura.io/jwt/claims", "hasuraLambdaId": "#{UUID()}", "issuer": "company.com", "mailServerHost": "smtp-host", "mailServerPassword": "smtp-pwd", "mailServerPort": 1025, "mailServerSecurity": "NONE", "mailServerUsername": "smtp-user", "registrationVerificationEmailTemplateId": "#{UUID()}", "serverlessApiKey": "42f41c94-e41a-492c-891c-c85f2204c639", "setPasswordEmailTemplateId": "#{UUID()}", "verificationEmailTemplateId": "#{UUID()}" } }I have defined a super-user api key:
Using that key, with python fusionauth client, I am trying to get all tenants like this:
response = client.retrieve_tenants() tenants = response.success_response['tenants']I get
Nonetenants. Why? I was expecting to see my default tenant here. Then, if I grab my default tenant id and use it like this:request = { 'tenant': { 'emailConfiguration': { 'host': hostname, 'port': port, 'username': username, 'password': password, 'security': 'SSL' if enable_ssl == 'true' else 'NONE', } } } response = client.update_tenant(tenant_id, request)then I get
response.status == 405which is not documented in your documentation. Why do I get that status? How can I update my default tenant's smtp parameters through the API? If I do it through the FusionAuth dashboard, then it works.I am working with FusionAuth
 version 1.32.1.
version 1.32.1.Thanks in advance for your help!
-
RE: how to kickstart an application with specified uuid?posted in Q&A
Hey Dan,
Thanks for your very useful advice. This line is critical in the configuration you mention:
"url": "/api/application/#{joomlaAppId}",I didn't know I could put the request parameter right there. My problem is then solved.
-
how to kickstart an application with specified uuid?posted in Q&A
Hi,
In my kickstart.json, I have the following section:
{ "body": { "application": { "jwtConfiguration": { "accessTokenKeyId": "#{accessTokenSigningKeyId}", "enabled": true, "refreshTokenTimeToLiveInMinutes": 1440, "timeToLiveInSeconds": 3600 }, "lambdaConfiguration": { "accessTokenPopulateId": "#{hasuraLambdaId}" }, "loginConfiguration": { "allowTokenRefresh": true, "generateRefreshTokens": true, "requireAuthentication": true }, "name": "test-application", "roles": [ { "isDefault": true, "isSuperRole": false, "name": "user" }, { "isDefault": false, "isSuperRole": false, "name": "manager" } ] } }, "method": "POST", "url": "/api/application" }In that kickstart, I would like to directly register a user in that application
test-application. I figured I could set myself the application's id (with e.g.#{UUID()}) and use that id in the user registration:{ "body": { "registration": { "applicationId": "#{THE_TEST_APPLICATION_ID}", "roles": [ "manager" ] }, "user": { "email": "#{managerEmail}", "password": "#{managerPassword}" } }, "method": "POST", "url": "/api/user/registration" },However, I was not able to gather from the documentation how to achieve that. The applicationId is a request parameter and there seems to be no way to set it through a parameter in the
/api/applicationbody.Is there a to do what I want or do I have to register the user after fusionauth kickstart?
Thanks in advance for your advice!
-
How to upgrade on k8s?posted in Q&A
Hi,
Provided I have deployed fusionauth on my kubernetes cluster, like this:
helm install --name fusionauth fusionauth/fusionauth --namespace ${AUTH_NAMESPACE} -f values-production.yaml --waitwith e.g. the following configuration
# values-production.yaml image: tag: 1.16.0 database: setupInitialState: false user: AUTH_DB_USERNAME password: AUTH_DB_USERPASSWORD host: AUTH_DATABASE_HOSTNAME port: AUTH_DATABASE_PORT name: AUTH_DATABASE_NAME root: user: AUTH_ROOT_USER password: AUTH_ROOT_PASSWORD search: engine: database ingress: enabled: falseWhat is my option to upgrade to the latest version (with data in the database)? Do I just uninstall the current helm chart and install the latest one? or is there a better option?
Thanks in advance
-
Is there a way to export current configuration to a kickstart file?posted in Q&A
Hi,
I have come up with some configuration of my fusionauth instance. Now I would like to export that configuration to a kickstart json file. Is it possible? That'd be pretty handy to have a solution for such a use case. I am currently experimenting with fusionauth, and I'd be glad to have a solution to pack my current config in a json file.
Thanks in advance for some hints!
-
RE: Kubernetes deployment of version 1.16.0-RC.1posted in Q&A
Interestingly, I installed version 1.16.0 today on its dedicated server, i.e. not on kubernetes, and there I have the very same problem as on kubernetes now: no way to connect with any browser than edge or explorer. Therefore, I think I was wrong, it's not a problem with my kubernetes settings. It seems to be an issue with either the fusionauth settings or the nginx load balancer. And with edge / explorer, even if I can login / logout as I wish, I cannot do anything with the software. I can't e.g. add an application, I get an Unauthorized access, even though I'm logged in with the admin account.
-
RE: Kubernetes deployment of version 1.16.0-RC.1posted in Q&A
@dan Yes, I will file a bug there if it is still happening. Thanks for your help.
-
RE: Kubernetes deployment of version 1.16.0-RC.1posted in Q&A
@dan said in Kubernetes deployment of version 1.16.0-RC.1:
Also, what in particular doesn't work with the current charts? What doesn’t support 1.16.0-rc.1?
Exactly this. I am using version 1.16.0-RC.1 because I don't want elasticsearch. Currently, the official charts do not allow to install it without elasticsearch.
-
Kubernetes deployment of version 1.16.0-RC.1posted in Q&A
Hi,
I'm a new user of fusionauth with absolutely no XP with that piece of software.
On the one hand, I have a kubernetes cluster where I have installed fusionauth. I've written my own helm chart as there are currently no official chart supporting installation of version 1.16.0-RC.1 (as far as I know). Fusionauth works fine on that cluster: I can access the dashboard and then do my stuff.
I was, on the other hand, also able to install fusionauth on a dedicated server separate from my kubernetes cluster. It also works fine, I can do the same stuff as with the instance installed in the k8s cluster.
Yet I have a problem. The only way I can log into the admin console on my k8s cluster is with Microsoft Edge or Microsoft Internet Explorer. It works for some time with Chrome, Safari, and Firefox, but after a few logins / logouts, it doesn't work anymore. I get indeed a 403 access denied. With Edge and Explorer, it works all the time.
On my separate server, it works with all browsers all the time.
In front of my k8s cluster and my separate server, I've put both times an nginx load balancer, on which I installed the let's encrypt certificates and configured SSL the same way (same
nginx.conf, samessl.conf).So, the only difference between the two environments is probably the additional nginx ingress controller on my k8s cluster. What can I do to further investigate that problem and find out its root cause? Does anyone have XP on k8s deployments of fusionauth? I'm running out of ideas ...