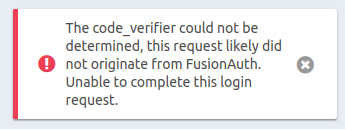
@mark-robustelli Sure!
I do the following (I use HTTPie)
- First I hit the
authorizeendpoint:http "https://myurl/oauth2/authorize?client_id=<myappid>&idp_hint=<myidpid>&nonce=<random generated nonce>&redirect_uri=/admin/login&response_type=code" - That gives me a
Locationwhich I follow:http "https://myurl/oauth2/redirect?client_id=<myappid>&identityProviderId=<myidpid>&state=<state>&nonce=<random generated nonce>" - Now again in the
LocationI get redirected to my IdP, I open that link in the browser and go through the flow of my IdP, once successfully authenticated it redirects me back tohttps://myurl/admin/login(the initial redirect URI) and I get the error I pasted earlier
Does this look correct to you?